Estimates of the number of Social Engineering based cyber-attacks into private or government organizations
- Details
- Category: Social Engineering
- Published: Monday, 14 May 2018 14:16
Written by Enrico Frumento, CEFRIEL
Today, only about 3% of malware tries to exploit an exclusively technical flaw. The other 97% involves targeting users through social engineering (source KnowBe4), i.e. an approach in which attacks use humans as channels to reach their target. Hacking attempts focused on human vulnerabilities in a system instead of lapses in software or hardware.
This is an improving trend, the “Phishing activity trends report. Unifying the global response to Cybercrime”, periodically released by the Anti Phishing Working Group (APWG) [16][17] reports what is in Figure 1.

Figure 1 – Statistics reported by APWG for Q2 and Q4 2016. CEFRIEL’s elaboration of the APWG data reported in the periodic “Phishing activity trends report. Unifying the global response to Cybercrime” [16][17]
Exact percentagewise estimates as the one above may vary, but it is a fact that the majority of the cyberattacks are designed to take advantage of human errors instead of flaws in hardware or software. According to ProofPoint (a leading cyber security company) Human Factor Report 2018 “human vulnerabilities are more dangerous to modern organizations than software flaws” [1]. All the sectors are equally hit by this plague, and equally vulnerable.
Targeted Attacks (TAs) are among those that efficiently exploit Social Engineering (SE) techniques to facilitate data breaches and exploits in general [2]. TAs are not the most widely used, but they are the most successful as they have the highest likelihood [2][3] of leading to data breaches in hospitals [3], public bodies [4] and in general all the business sector are equally vulnerable. As an example of how the social engineering is spread across the different sectors, are the data from KnowBe4, for the US market (see Figure 2) and Cefriel, for the EU, see the information that R.Puricelli reported in [5], see Figure 3. DOGANA results will be published in the coming months.

Figure 2 - KnowBe4 statistics of their simulated phishing tests (updated Jan 2018) Source: KnowBe4
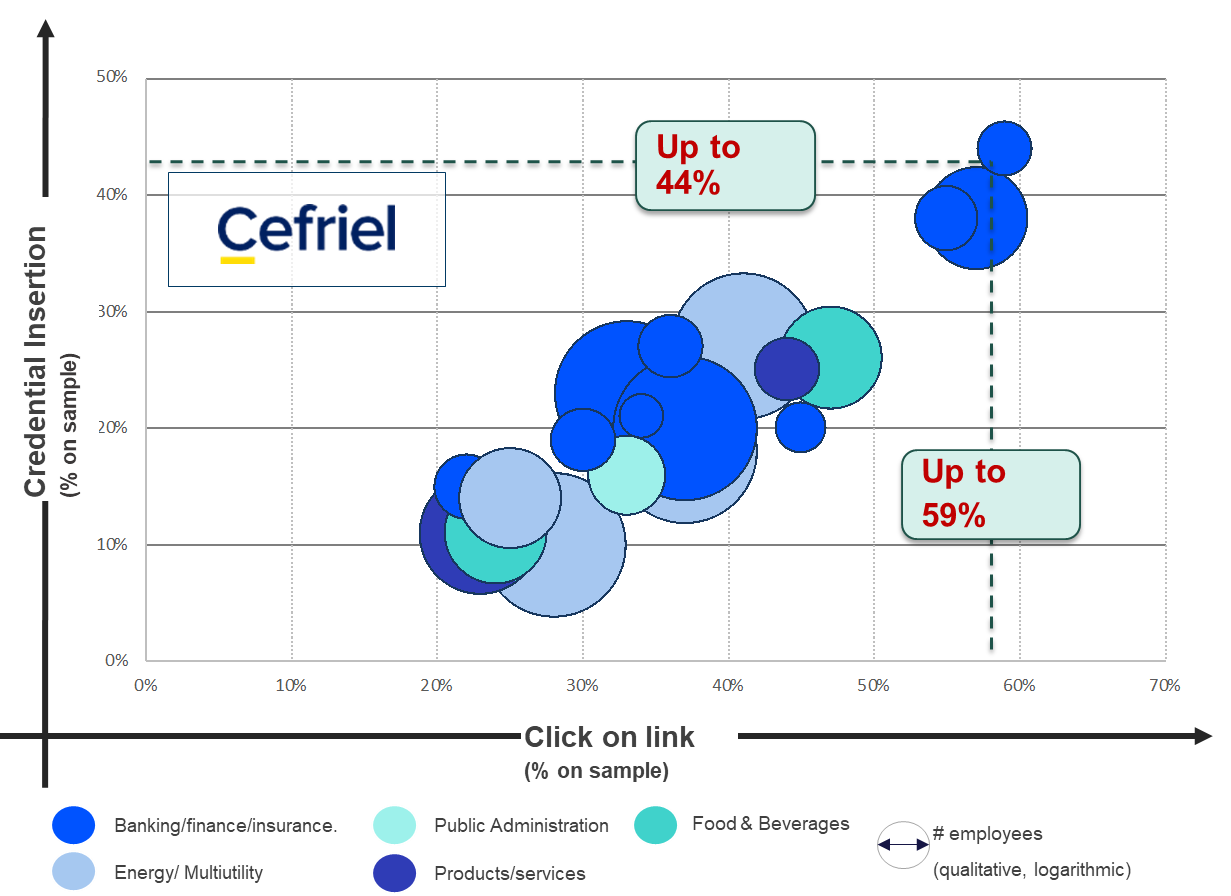
Figure 3 – CEFRIEL’s statistics of the performed SDVAs (Source: CEFRIEL [5])
Estimate of the cost to companies, governments and/or the economy due to social engineering cyber attacks
The costs of social engineering are the costs of any cyber-attack. The biggest portion of today’s threat landscape (according to studies always above 90%) involves attacks whose “kill switch” resides outside the ICT domain and whose mitigation requires actions on the humans or, in other words, hardening the human layer of security. As shown by the DOGANA Project [2], the complexity level of attacks that actively exploit the human element is incredibly high and often the exploitation of the human element is the enabler element for the following technological part of an attack. However, Social Engineering is also evolving and today we are talking of SE 2.0 vs old school SE [4]. Social Engineering (SE) is the human-side of hacking and we are currently in the “era” of human hacking [4]. Recent studies report that among the 5 biggest threats, 3 out of 5 are social engineering based and for them a training remediation would have worked. Unfortunately, cybercrime is also “moving to the humans” at the same, or even faster, pace: the so-called human layer of security has become, in recent years, the number one tactic to launch successful attacks, across industries worldwide. Today, only about 3% of malware exploit a technical flaw. The other 97% trick users through Social Engineering [8].
Hence, the elements of the equation are simple:
- For more than 90% of the successful attacks human are the “kill switch”. This means that without the human error the attack won’t start
- According to CyberEdge [6], the number of successful attacks has risen the last three years from 62% in 2014, to 71% in 2015, to 76% in 2016, and to 79% in 2017 with no end in sight. 91% of these attacks use spear phishing
- According to FireEye [7], the average time from an email phishing breach to detection is 146 days globally, and a colossal 469 days for the EMEA region. According to the report, “At a basic level, the notion that hackers are rooting around in companies’ networks undetected for 15 months is sobering, as it allows ample opportunity for lateral movement within IT environments.”
The conclusion is that the consequences of a cyber-attack leveraging on the human element of security are enormous, much more than any other type of cyber-attack probably, also because there is no 100% fully working solution in sight. “Patching” the humans or, more formally, influence the behavioural traits of the human layers of security, is not an easy task and requires investments and most of all research.
Hardening of the human element is at the centre of successful strategies. Whilst often industry workers lack basic cybersecurity or cyber-hygiene training, the technological countermeasures (e.g. automated anti-deception systems) are not reliable or scalable enough to reduce the risk to a manageable level. Human based countermeasures are still required. This means effective solutions for training. Actually, training is the only preventive defence strategy for the human layer of security [9].
However, the existing training solutions are not adequate, because they are not able to permanently change the human behaviour in a predictably and a-priori measurable and lasting way [10][11][12].
Early results of the Social Driven Vulnerability Assessments (SDVA) performed during the DOGANA project [13] clearly show that not all training programs perform well, leaving the final risk for enterprises unchanged on the long run. As an example, ProofPoint [14] in 2015 reported, “People clicked on test phishing campaigns in 2014 because they did not match the characteristics they had been trained to look for in 2013”. Another research reports the results of a phishing test run on a big sample of enterprise employees [15] before and 3 months after an awareness program. It clearly shows that the risk level was reduced immediately, but increased again after 3 months.
Do we know whether the EU is funding other projects in Social Engineering? If so, do we have an idea of the total investment of the EU (Horizon2020) in this area?
To my knowledge DOGANA is the only financed project directly targeting the problem of social engineering from the ICT security point of view. The project HERMENEUT (Enterprises intangible Risk Management via Economic models based on simulation of modern cyber-attacks www.hermeneut.eu) adds beside DOGANA the econometric models, in order to evaluate the economic impact of a cyber-attack in general terms. Which also answers to the Question 2. The HERMENEUT project inherits several key partners from the DOGANA project because the research question is huge and complex.
Would it be possible to reach a 100% effectiveness ratio, which means corrupt all the employees, using social engineering attacks?
Due to legal and ethical reasons, an SDVA cannot push the pedal to the metal and deeply contextualize the SDVAs, wrapping them around each single victims. In other words, an SDVA should not simulate a real context aware phishing attack. It is possible and feasible, but not legal, neither ethical.
The question is therefore partially theoretical, within the European legal framework. Under these assumptions, the question becomes which is the semantic distance among the real emails and the emulated phishing. If we define the semantic distance as the distance in terms of content relevance for the victim, between real and phishing emails, we can state that the lower this distance is, the higher the percentage of victims is. If we are able to build 100% contextualized email and deliver a fully contextualized phishing email to each employees, so as it is, semantically speaking, indistinguishable by a real email, then phishing effectiveness tends to be 100%. This is intimately connected to the nature of humans and is something that is hardly solvable today.

Figure 4 – Correlation between effectiveness of (simulated) phishing attacks and the semantic distance between phishing and real email
[1] ProofPoint, “The Human Factor Report 2018, people-centered threats define the landscape”, April 2018,
[2] AA.VV. “D2.1 - The role of Social Engineering in evolution of attacks”, DOGANA Advanced Social Engineering and Vulnerability Assessment Framework (2016)
[3] "Spear-Phishing and Health Care Organizations", Symantec, 2018.
[4] E. Frumento, “What the Enterprises can do to measure and mitigate the latest evolutions of Social Engineering,” https://medium.com/our-insights/what-the-enterprises-can-do-to-measure-and-mitigate-the-latest-evolutions-of-social-engineering-938c62143918
[5] R. Puricelli, “The Underestimated Social Engineering Threat in IT Security Governance and Management”, https://www.isaca.org/Journal/archives/2015/Volume-3/Documents/The-Underestimated-Social-Engineering-Threat-in-IT_joa_Eng_0515.pdf
[6] CyberEdge CDR Report, 2017, https://cyber-edge.com/wp-content/uploads/2017/06/CyberEdge-2017-CDR-Report.pdf
[7] FireEye, https://www.fireeye.com/content/dam/fireeye-www/global/en/current-threats/pdfs/rpt-world-eco-forum.pdf
[8] “What is Social Engineering?”, knowbe4.com, 2018.
[9] J. Rennecker, “Healthy Skepticism – Your Best Cyber Defense”, Third Rock, 2017.
[10] “Is cybersecurity awareness a waste of time?”, New Zealand Reseller News, 2018.
[11] T. Qin and J. K. Burgoon, “An investigation of Heuristics of human judgment in detecting deception and potential implications in countering social engineering,” IEEE Intelligence and Security Informatics, May 2007.
[12] M. Buratowski, “Instilling a culture of cyber security”, Help Net Security, 2015.
[13] E.Frumento, R.Puricelli. “An innovative and comprehensive framework for Social Driven Vulnerability Assessment”, In S. Schumacher and R. Pfeiffer (Editors), In Depth Security: Proceedings of the DeepSec Conferences (pp 15–36)
[14] “The Human Factor 2015,” in Proofpoint, 2015.
[15] E. Frumento, C. Lucchiari, A. Valori, and G. Pravettoni, “Cognitive approach for social engineering,” in DeepSec, Web, 2010.
[16] http://docs.apwg.org/reports/apwg_trends_report_q2_2016.pdf
[17] http://docs.apwg.org/reports/apwg_trends_report_q4_2016.pdf
by Enrico Frumento (CEFRIEL)





